Azure configuration
This document describes how to set up an IPsec connection with WALLIX One PAM and your platform hosted on Azure using either static or dynamic routing.
Prerequisite
WALLIX One PAM side
You need some information about your WALLIX One PAM platform:
- IPsec endpoint address
- Subnets
- BGP ASN (if you use dynamic routing)
For this example, we use the following values:
- IPsec endpoint address: 20.199.96.10
- Subnets:
- 100.64.12.0/25
- 100.64.13.0/25
- 20.199.99.129/32
- BGP ASN: 210094 (if you use dynamic routing)
Azure side
A resource group with vnet and subnet must already exists. In this example:
- resource group: wallix-w1pam
- vnet: wallix-w1pam-vnet (10.1.0.0/16)
- subnet: create dedicated subnet for VPN gateway. This subnet need to be named 'GatewaySubnet' and use /27 or /28.
Configuration with dynamic routing (BGP)
IMPORTANT
Currently, WALLIX w1pam only provides a single VPN instance.
In the future, a second instance must be added to provide high availability between W1P and your remote sites.
IMPORTANT
Currently, WALLIX w1pam does not support peering 2 connections with the same Azure virtual private gateway in dynamic routing mode.
Dynamic routing mode does not support high availability.>
Virtual network gateway
Create a virtual network gateway 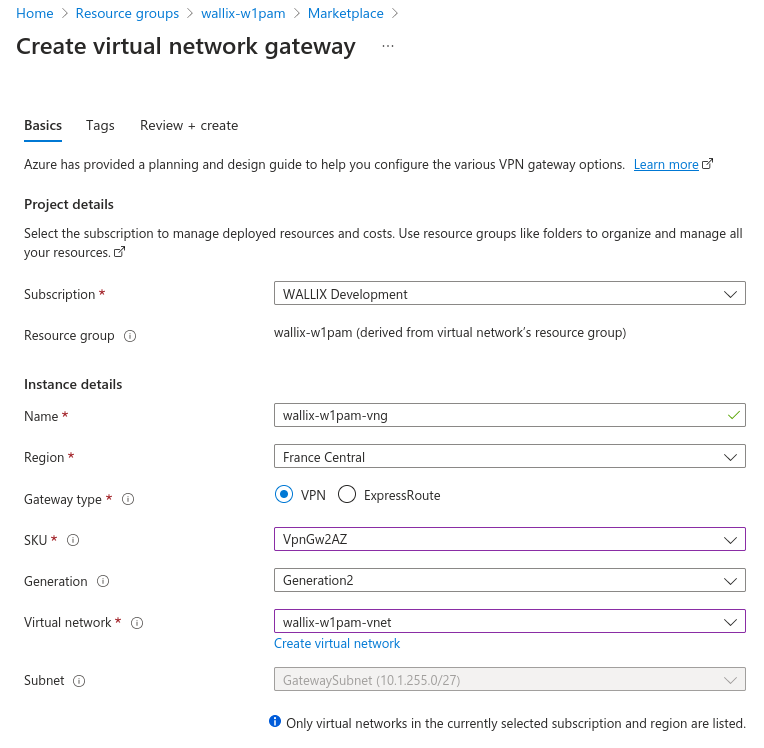
Parameters:
- Name: wallix-w1pam
- gateway type: VPN
- SKU: VpnGw2AZ
- Generation: Generation2
- Virtual network: select target vnet
- Gateway subnet address range: your 'GatewaySubnet' must appear
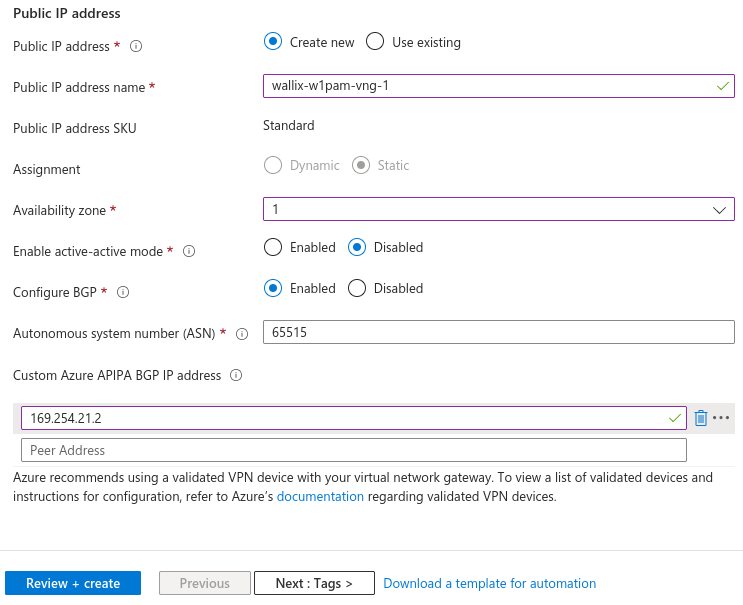 Parameters:
Parameters:
- Enable active-active mode: Disabled
- Configure BGP: Enabled
- ASN: use any ASN number
- APIPA BGP IP address: 169.254.21.2
Check configuration and create.
After few minutes (~15), VPN gateway must be available.
Local network gateway
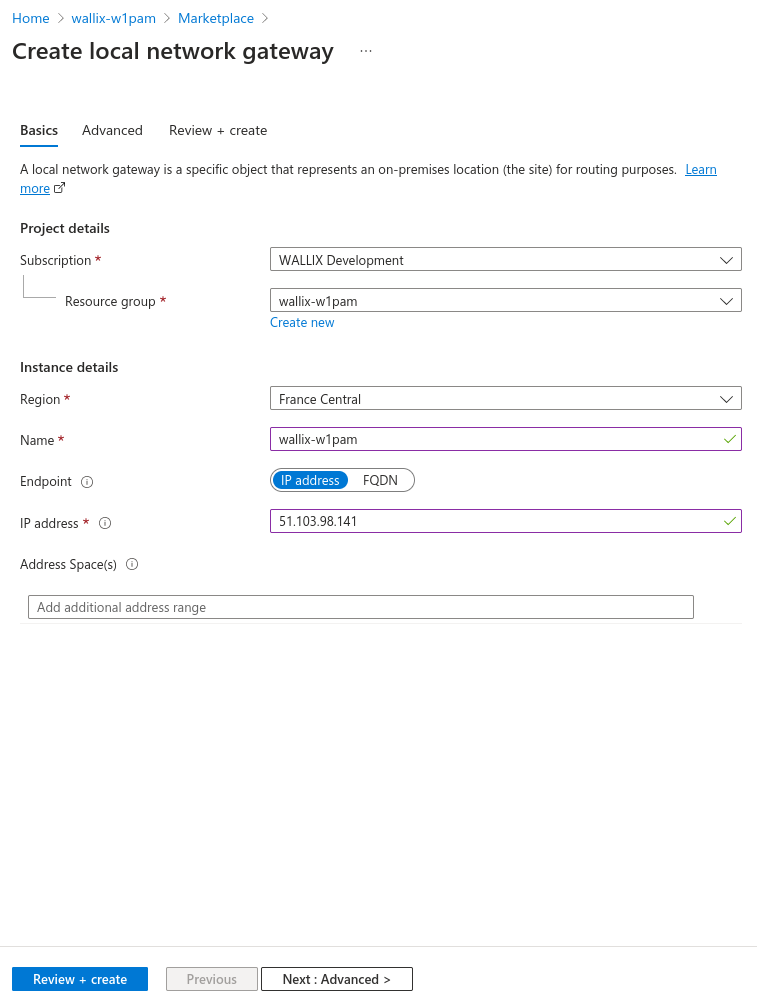 For "IP address" fields, put public ip address of WALLIX One PAM IPsec service specified on prerequisite.
For "IP address" fields, put public ip address of WALLIX One PAM IPsec service specified on prerequisite.
 On basic step:
On basic step:
- ASN: put BGP ASN of WALLIX One PAM IPsec service specified on prerequisite
- peer IP address: 169.254.21.1
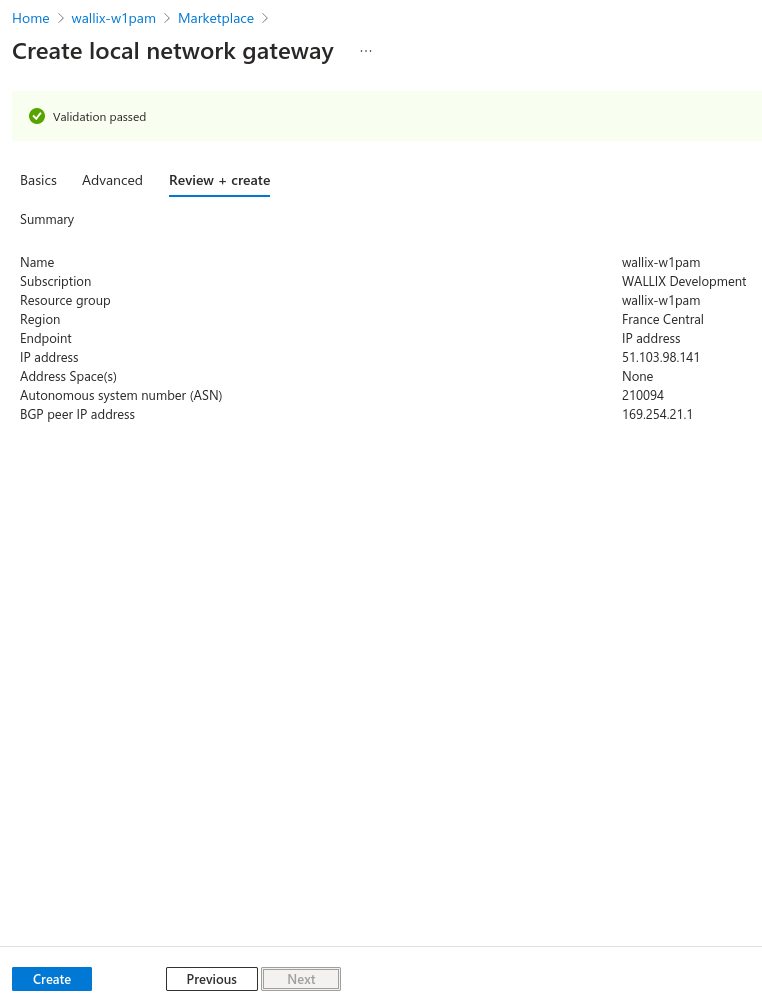 Validate informations and click on "Create".
Validate informations and click on "Create".
VPN connection
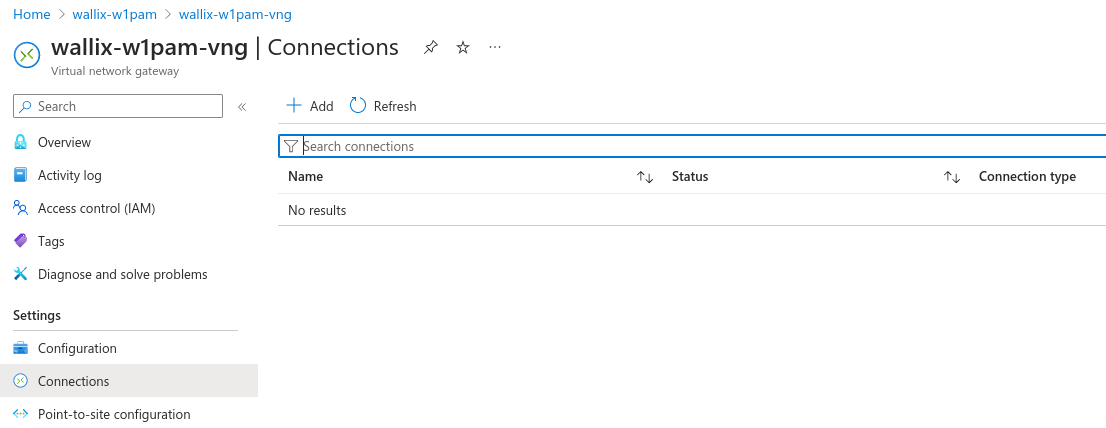 Add VPN connection to "wallix-w1pam-vng" virtual network gateway.
Add VPN connection to "wallix-w1pam-vng" virtual network gateway.
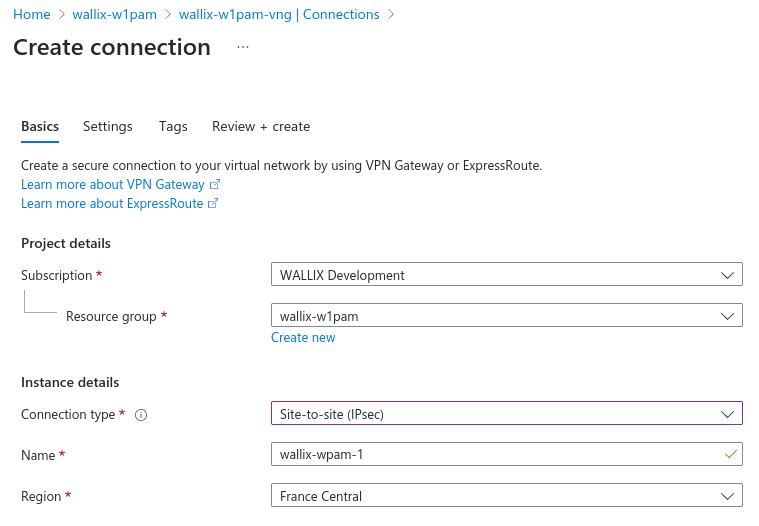 Configure basic informations.
Configure basic informations.
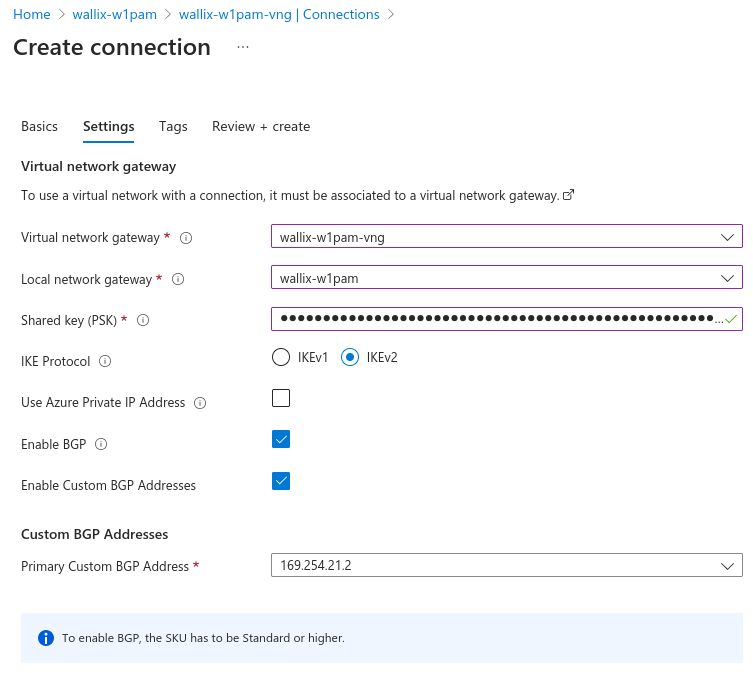 Configure settings:
Configure settings:
- PSK: put a PSK that only contains letters (lowercase and uppercase), numbers, and underscores, with a size between 32 and 128 characters.
- IKE protocol: selection IKEv2
- Enable BGP and custom BGP addresses
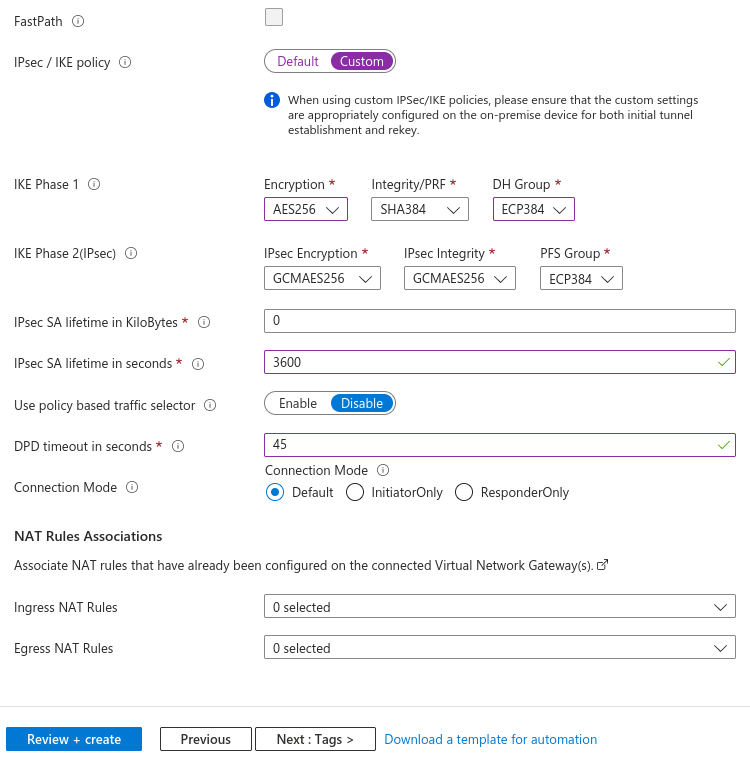 Complete all options. Select the best encryption, integrity, and DH Group supported by your IPsec endpoint
Complete all options. Select the best encryption, integrity, and DH Group supported by your IPsec endpoint
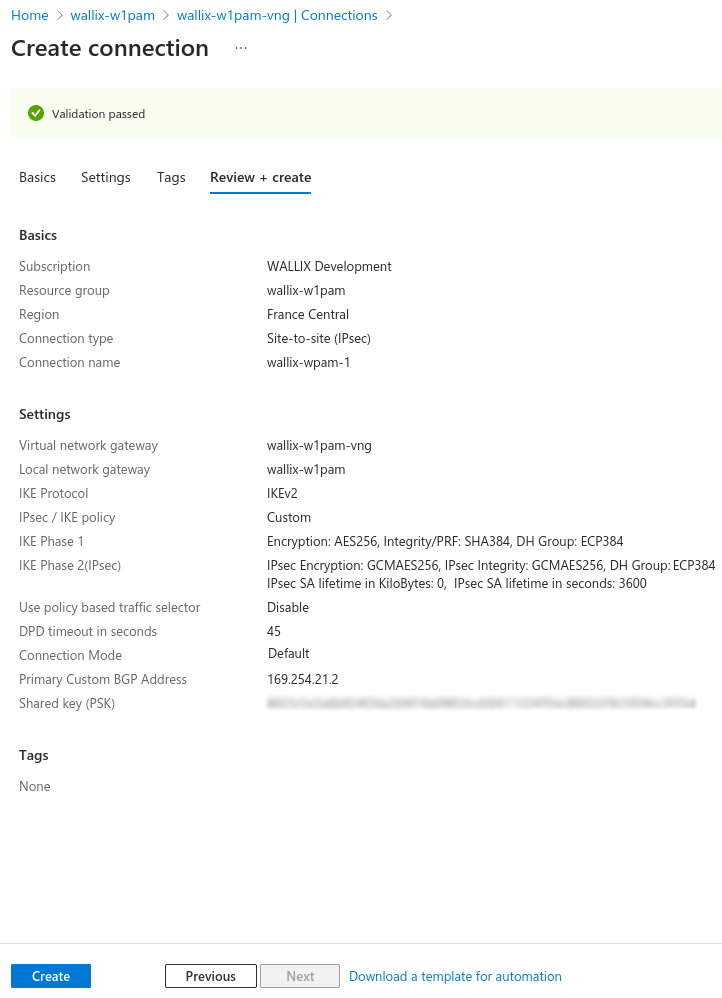 Verify informations and create connection.
Verify informations and create connection.
Send configuration to WALLIX support
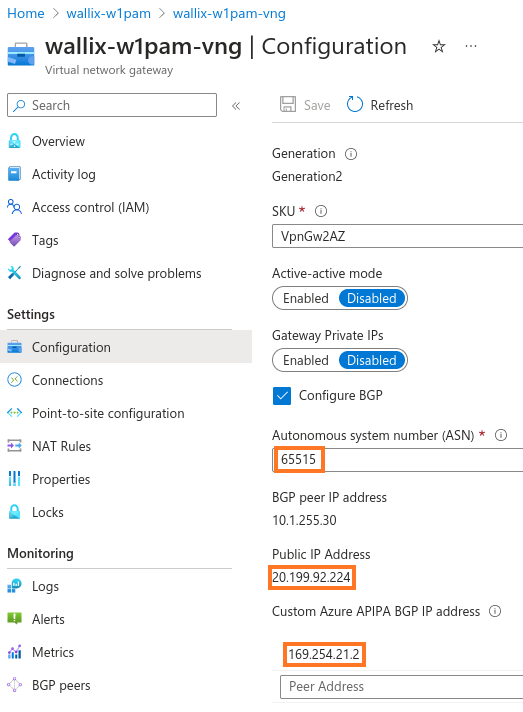
The following information must be declared in the shuttle document for the configuration of the IPsec tunnel:
- name: choose a name for this tunnel (e.g., azure-1)
- ip_address: public ip address of the Azure virtual network gateway (e.g., 20.199.92.224)
- tunnel_cidr: Use the value of 'Custom Azure APIPA BGP IP address' retrieved in the configuration and substitute 1 for the last octet + "/30" (e.g., 169.254.21.0/30).
- use_first_address: True
- bgp_asn: the ASN defined previously when the new router was created (e.g., 6515)
- psk: the pre-shared key defined previously
- phase1_ciphers: AES256.
- phase1_integrity: SHA2-384
- phase2_ciphers: AES256_GCM_16
- phase2_integrity: SHA2-384 (when used AES128_GCM_16 or AES256_GCM_16 phase2 integrity will not be used)
- dhs: 20
- routing_mode: "dynamic"
These settings must be provided to WALLIX support to establish the IPsec tunnel.
Check status
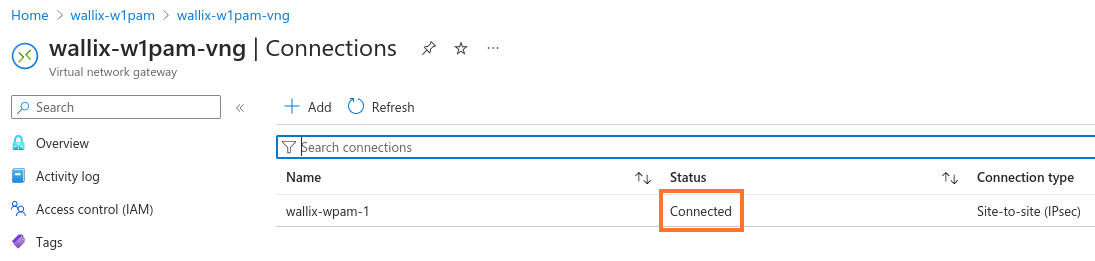 Status must be "Connected"
Status must be "Connected"
Check received routes
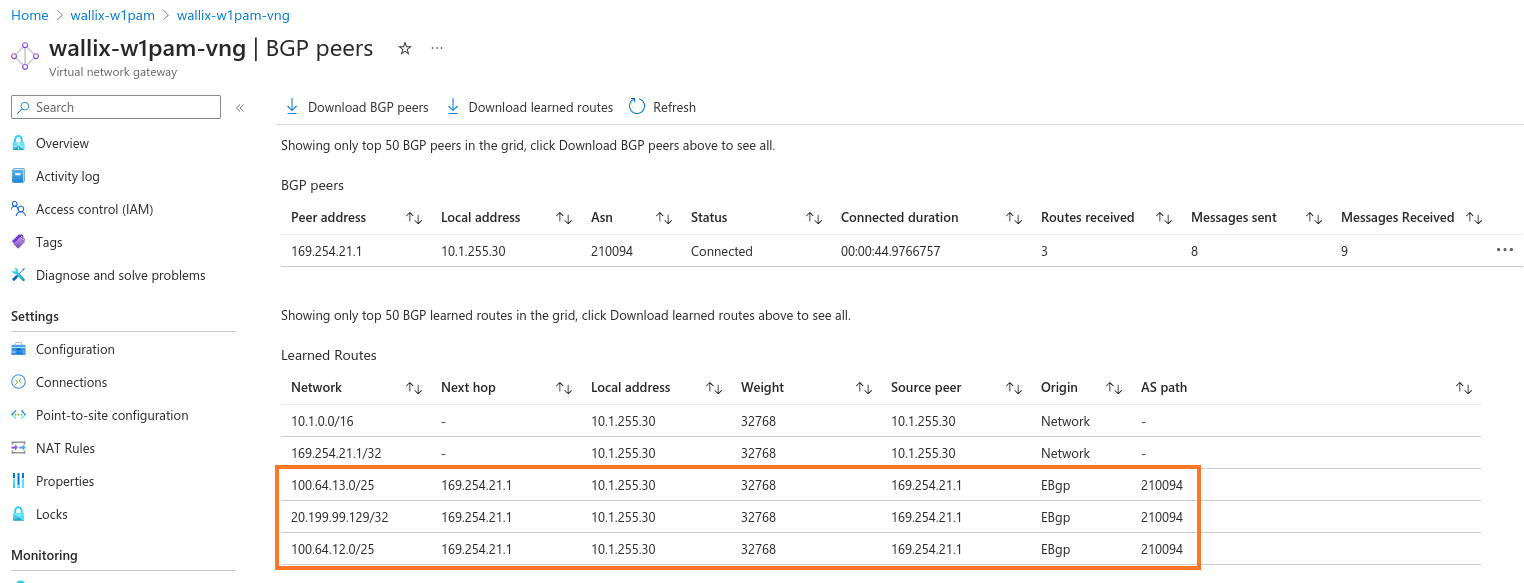 You must see three routes:
You must see three routes:
- 2 private subnets: used for outbound connections by Bastion and Access Manager
- 1 public address: used for incoming connections from users to Bastion or Access Manager
Configuration with static routing
IMPORTANT
Currently, WALLIX WALLIX One PAM only provides a single VPN instance.
In the future, a second instance must be added to provide high availability between W1P and your remote sites.
NOTE
Static routing mode must be used if you want safeguard against the failure of one of your gateway devices.
Virtual network gateway
Create a virtual network gateway 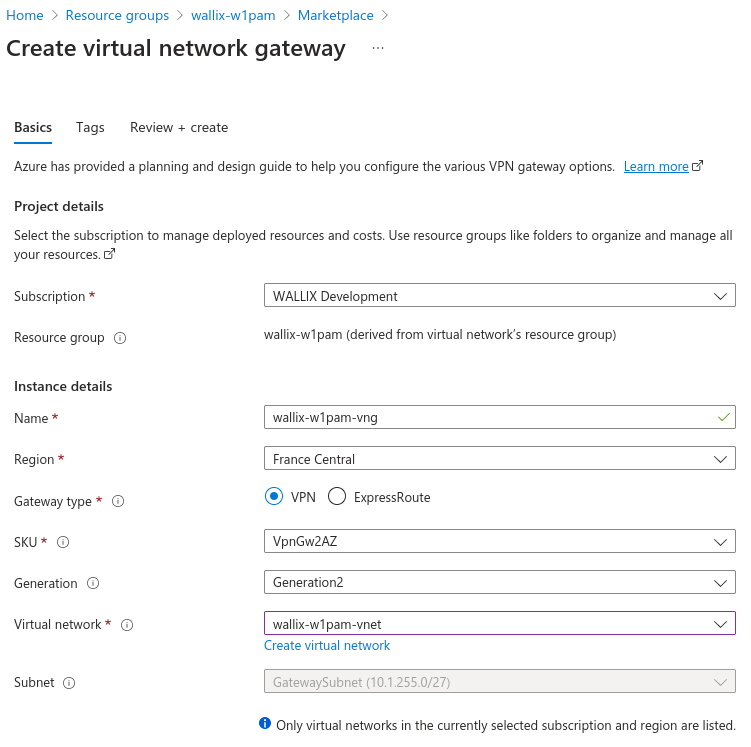
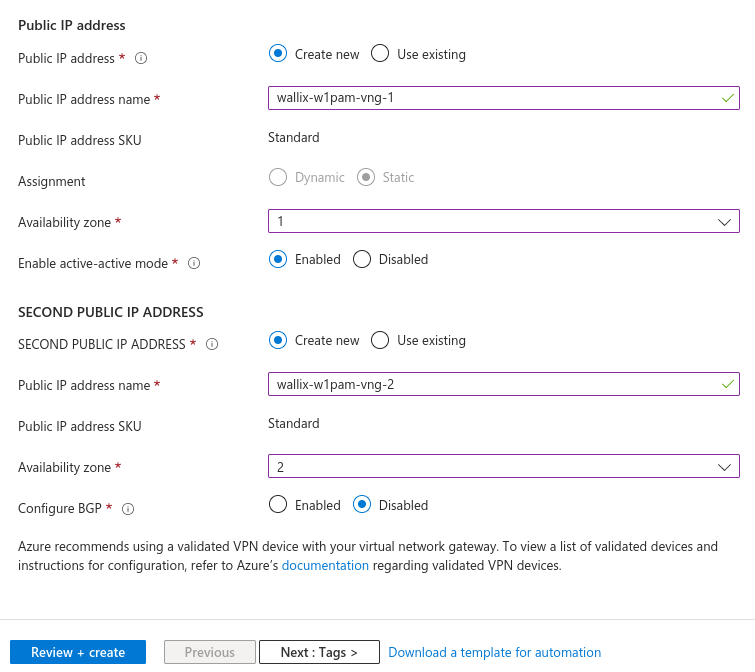
Check information and launch creation 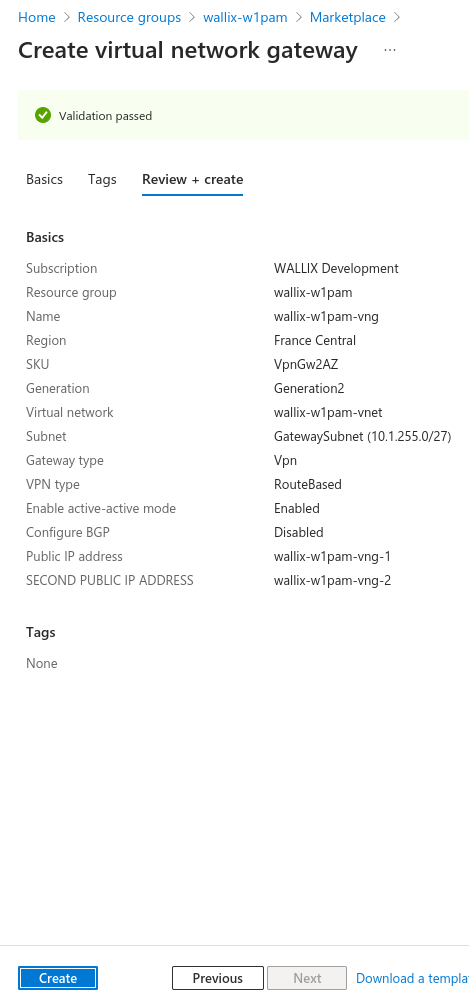
Local network gateway
Create local network gateway.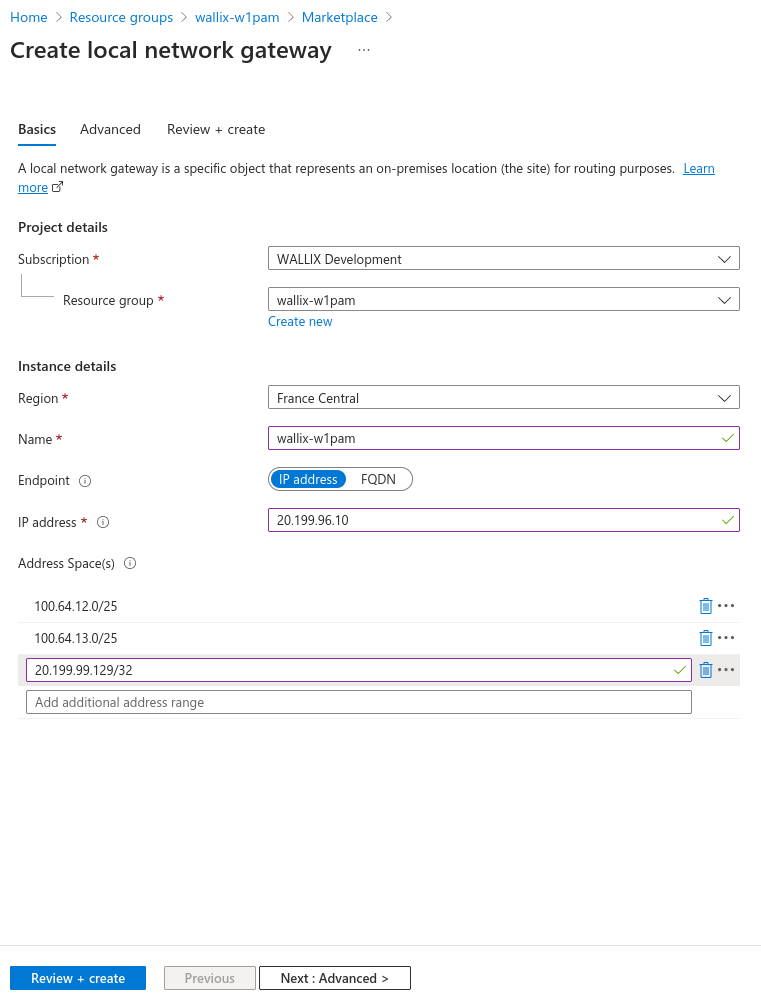 For "IP address" fields, put public ip address of WALLIX One PAM IPsec service specified on prerequisite.
For "IP address" fields, put public ip address of WALLIX One PAM IPsec service specified on prerequisite.
Put on "Address Space(s)" field all prefixes exposed by WALLIX One PAM provided by WALLIX support.
 Let BGP disabled.
Let BGP disabled.
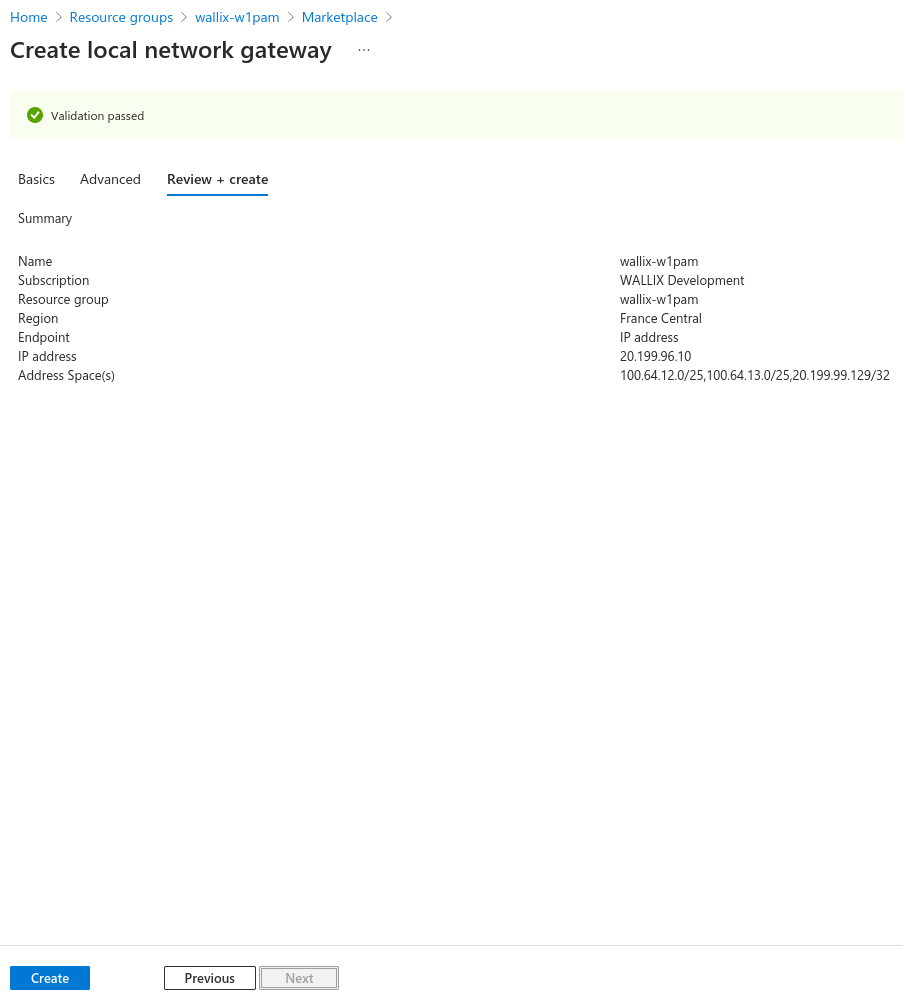 Validate informations and click on "Create".
Validate informations and click on "Create".
VPN connection
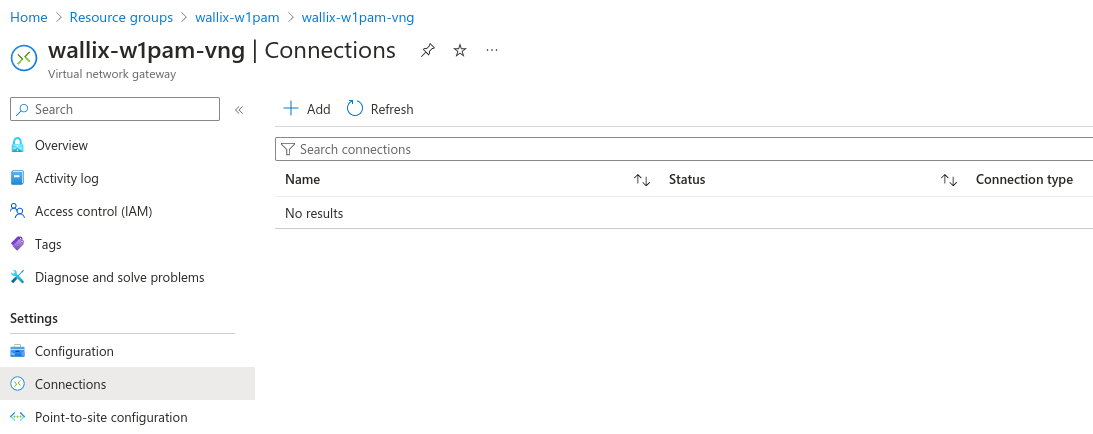 Add VPN connection to "wallix-w1pam-vng" virtual network gateway.
Add VPN connection to "wallix-w1pam-vng" virtual network gateway.
 Configure basic informations.
Configure basic informations.
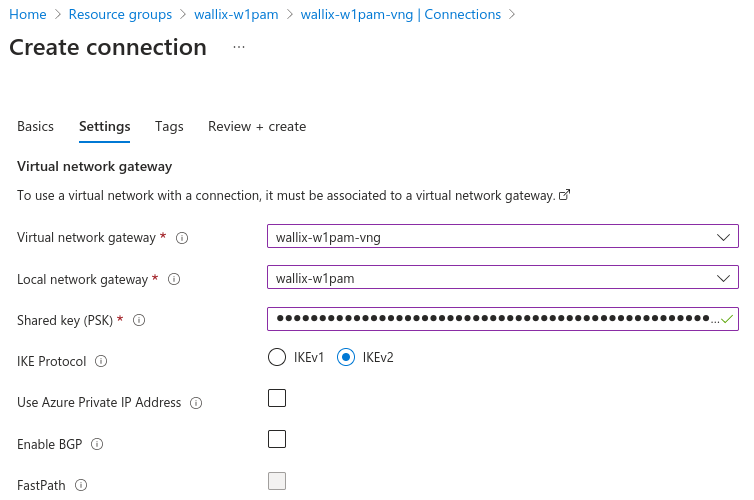 Configure settings:
Configure settings:
- PSK: put a PSK that only contains letters (lowercase and uppercase), numbers, and underscores, with a size between 32 and 128 characters.
- IKE protocol: selection IKEv2
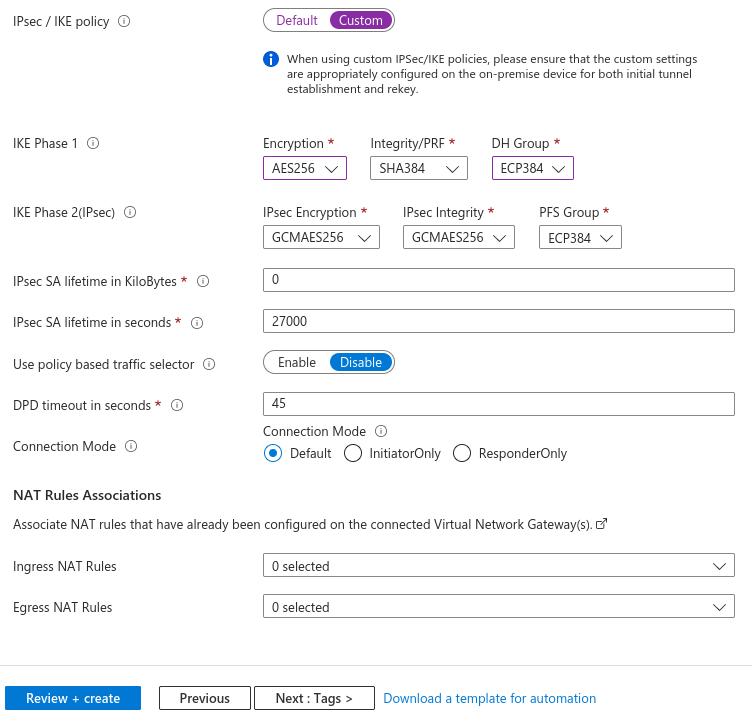 Complete all options. Select the best encryption, integrity, and DH Group supported by your IPsec endpoint
Complete all options. Select the best encryption, integrity, and DH Group supported by your IPsec endpoint
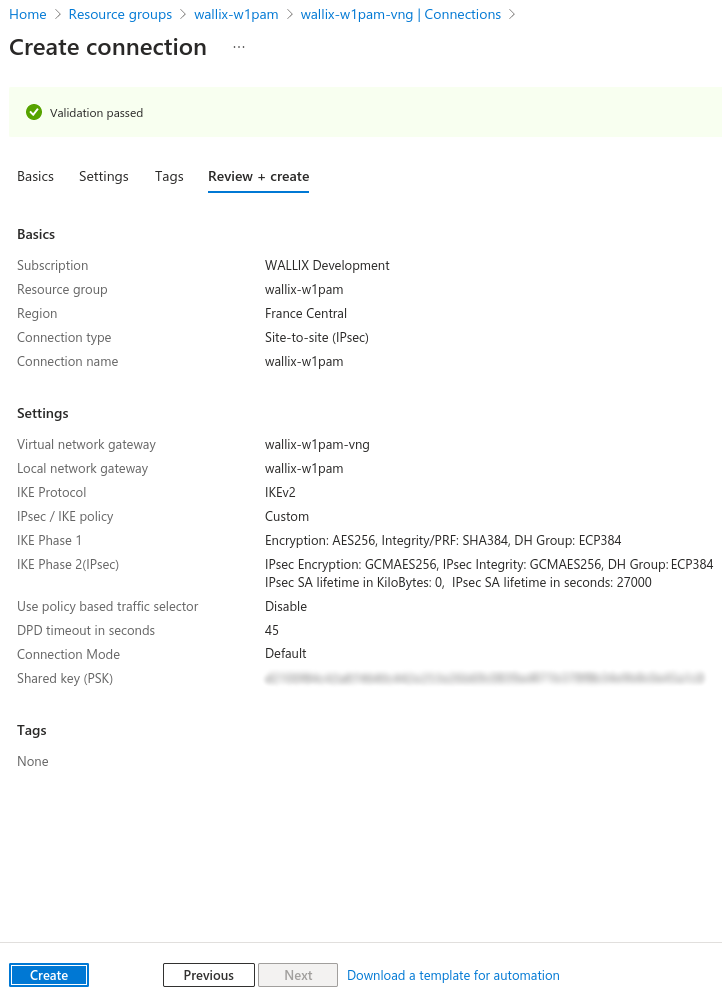 Verify informations and create connection.
Verify informations and create connection.
Send configuration to WALLIX support
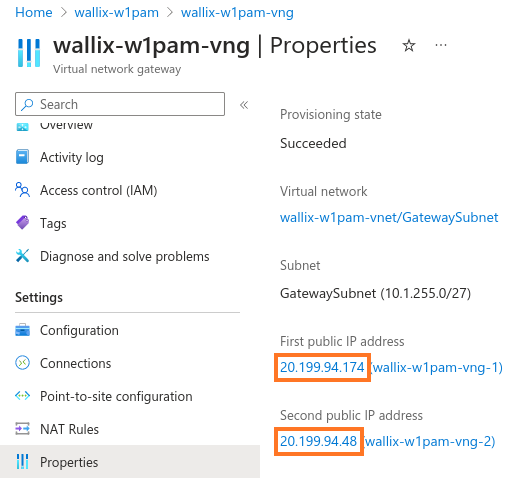
The following information must be declared in the shuttle document for the configuration of the IPsec tunnel 1:
- name: choose a name for this tunnel (e.g., azure-static-1)
- ip_address: public ip address of the Azure virtual network gateway (e.g., 20.199.94.174)
- psk: the pre-shared key defined previously
- phase1_ciphers: AES256.
- phase1_integrity: SHA2-384
- phase2_ciphers: AES256_GCM_16
- phase2_integrity: SHA2-384 (when used AES128_GCM_16 or AES256_GCM_16 phase2 integrity will not be used)
- dhs: 20
- routing_mode: "static"
- use_policy_based_traffic_selector: False
- phase2_subnets: subnets of the azure virtual network (e.g. ['10.1.0.0/16'])
The following information must be declared in the shuttle document for the configuration of the IPsec tunnel 2:
- name: choose a name for this tunnel (e.g., azure-static-2)
- ip_address: public ip address of the Azure virtual network gateway (e.g., 20.199.94.48)
- psk: the pre-shared key defined previously
- phase1_ciphers: AES256.
- phase1_integrity: SHA2-384
- phase2_ciphers: AES256_GCM_16
- phase2_integrity: SHA2-384 (when used AES128_GCM_16 or AES256_GCM_16 phase2 integrity will not be used)
- dhs: 20
- routing_mode: "static"
- use_policy_based_traffic_selector: False
- phase2_subnets: subnets of the azure virtual network (e.g. ['10.1.0.0/16'])
These settings must be provided to WALLIX support to establish the IPsec tunnels.
Check status
 Status must be "Connected"
Status must be "Connected"

