Architecture
Sites and WALLIX One PAM are connected together by establishing one or several tunnels. Tunnels must be considered for:
- sites where targeted devices and applicattions are located
- sites where local users and WALLIX One PAM administrators are located
IMPORTANT
The IPSec tunnel is initiated from the client’s network to WALLIX One PAM gateway, meaning no inbound connections or open ports are required on the client’s side.
NOTE
WALLIX One PAM does not require the installation of any on-premises connectors.
NOTE
The same tunnel can be used for local users' connection to WALLIX One PAM and for WALLIX One PAM bastion's connection to targeted devices.
Target access
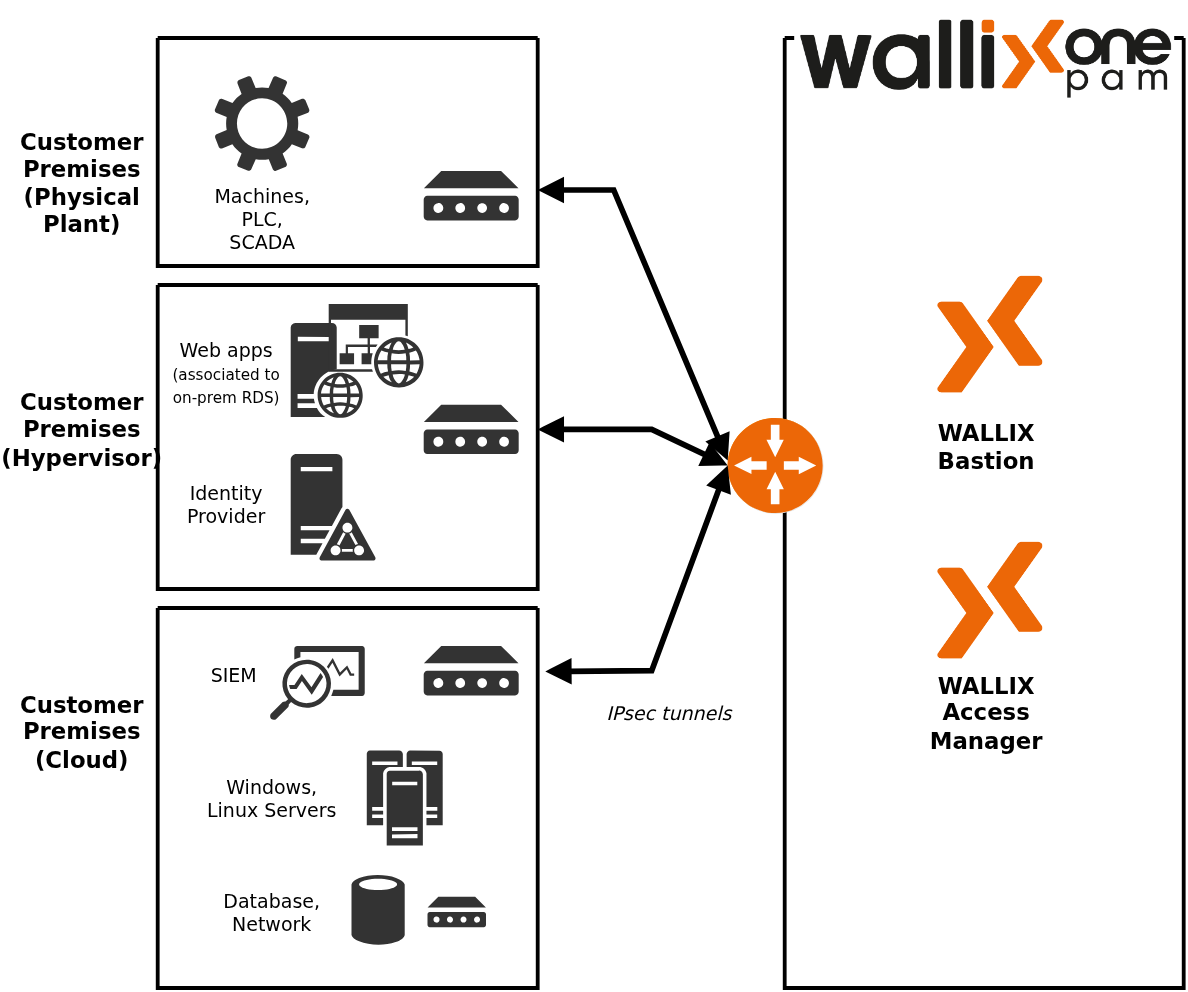
WALLIX One PAM can be connected to multiple sites and covers different environnements (hardware, hypervisor, cloud).
NOTE
To access web applications from WALLIX One PAM, it is necessary to deploy an on-premises Remote Desktop Services (RDS) farm. Refer to WALLIX Bastion administration guide for further details.
User access
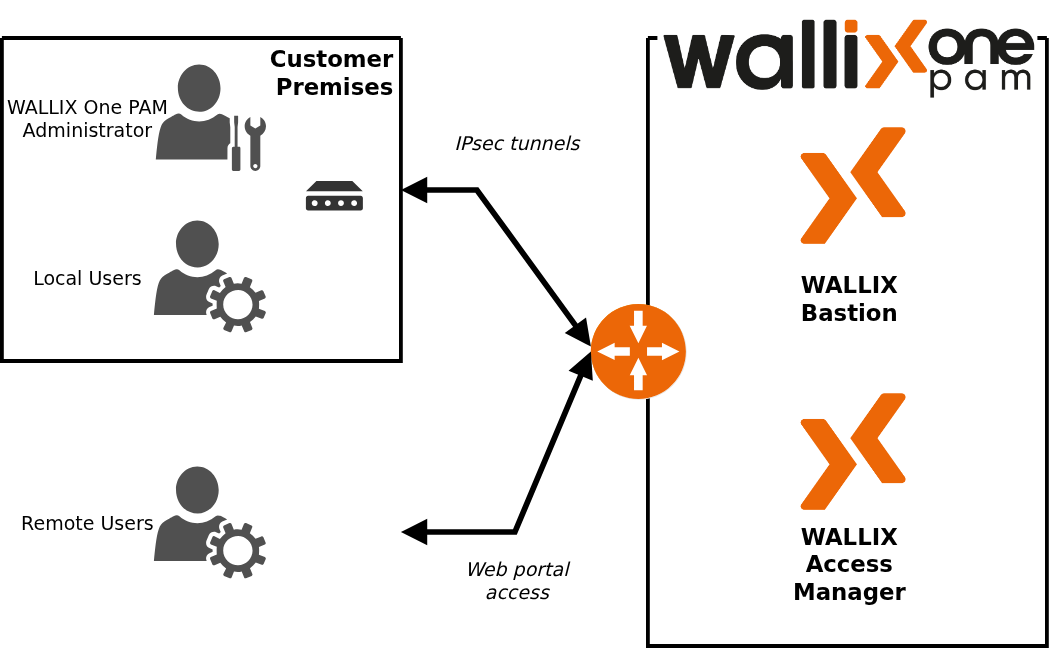
WALLIX One PAM enables access of local and remote users to targets. Solution administration is possible only for local users. For more details about access:
NOTE
With WALLIX One PAM Core, remote users cannot access targets from the web portal. Only local users can access targets from the customer premises.
Network flows
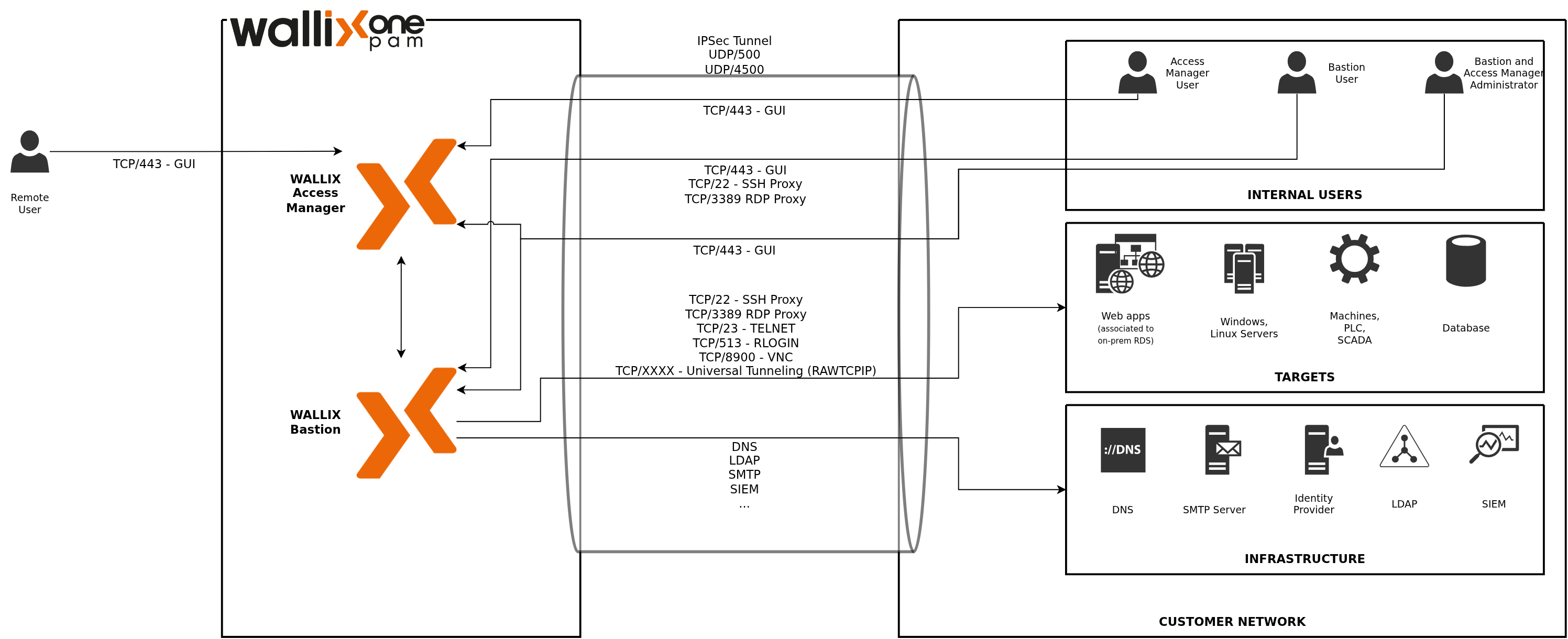
The following diagram represents the network flows between WALLIX One PAM and your infrastructure.
NOTE
By default, WALLIX One PAM does not allow outbound traffic to the Internet. To integrate with third-party services hosted in the Internet, WALLIX One PAM operators need to explicitly authorize outgoing Internet traffic.
This table lists the different network flows:
| Source | Destination | Protocol | Transport protocol/Port |
|---|---|---|---|
| External User | WALLIX Access Manager* | HTTPS | TCP/443 |
| User from company's network | WALLIX Bastion - GUI | HTTPS | TCP/443 |
| User from company's network | WALLIX Bastion - RDP Proxy | RDP | TCP/3389 |
| User from company's network | WALLIX Bastion - SSH Proxy | SSH/SFTP | TCP/22 |
| Administrator from company's network | WALLIX Bastion - GUI | HTTPS | TCP/443 |
| Administrator from company's network | WALLIX Access Manager - GUI* | HTTPS | TCP/443 |
| WALLIX Bastion | Target SSH | SSH/SFTP | TCP/22 |
| WALLIX Bastion | Target RDP/RDS | RDP | TCP/3389 |
| WALLIX Bastion | Target RDP Shadowing (4 Hands) | RDP | TCP/49152-65535 |
| WALLIX Bastion | Target VNC | VNC | TCP/5900 |
| WALLIX Bastion | Target | TELNET/RLOGIN | TCP/25 TCP/513 |
| WALLIX Bastion | PLC | OT protocols | TCP/102, TCP/502, ... |
| WALLIX Bastion | LDAP server | LDAP, LDAPS | TCP/389, TCP/636 |
| WALLIX Bastion | DNS server | DNS | UDP/53 TCP/53 |
| WALLIX Bastion | SIEM | SYSLOG | UDP/514 |
| WALLIX Bastion | Mail server | SMTP, SMTPS, STARTTLS | TCP/25, TCP/465, TCP/587 |
| WALLIX Bastion | Kerberos | KERBEROS | TCP/88, TCP/464 |
| WALLIX Bastion | Radius or TACACS | RADIUS, TACACS+ | TCP/1812, TCP/49 |
*Those flows don't exist for WALLIX One PAM Core.
NOTE
WALLIX One PAM does not enforce protocol filtering on outbound traffic over the IPSec tunnel. Clients are responsible for implementing any necessary filtering on their side of the tunnel to restrict outbound traffic to the protocols they use.

